Modern microservices architectures often require supporting both HTTP REST APIs and gRPC services simultaneously. While Google’s gRPC-Gateway provides HTTP and gRPC transcoding capabilities, the challenge of bidirectional header mapping between these protocols remains a common source of inconsistency, bugs, and maintenance overhead across services. This article explores the technical challenges of HTTP-gRPC header mapping, examines current approaches and their limitations, and presents a standardized middleware solution that addresses these issues.
Understanding gRPC AIP and HTTP/gRPC Transcoding
Google’s Application Programming Interface Improvement (AIP) standards define how to build consistent, intuitive APIs. For example, AIP-127: HTTP and gRPC Transcoding enables a single service implementation to serve both HTTP REST and gRPC traffic through protocol transcoding.
How gRPC-Gateway Transcoding Works
The gRPC-Gateway acts as a reverse proxy that translates HTTP requests into gRPC calls:
HTTP Client ? gRPC-Gateway ? gRPC Server
? ? ?
REST Request Proto Message gRPC Service
Following is the transcoding process:
- URL Path to RPC Method: HTTP paths map to gRPC service methods
- HTTP Body to Proto Message: JSON payloads become protobuf messages
- Query Parameters to Fields: URL parameters populate message fields
- HTTP Headers to gRPC Metadata: Headers become gRPC metadata key-value pairs
The Header Mapping Challenge
While gRPC-Gateway handles most transcoding automatically, header mapping requires explicit configuration. Consider this common scenario:
HTTP Request:
POST /v1/users Authorization: Bearer abc123 X-Request-ID: req-456 X-User-Role: admin Content-Type: application/json
Desired gRPC Metadata:
metadata.MD{
"authorization": []string{"Bearer abc123"},
"request-id": []string{"req-456"},
"user-role": []string{"admin"},
}
Response Headers Needed:
X-Request-ID: req-456 X-Processing-Time: 150ms X-Server-Version: v1.2.0
Without proper configuration, headers are lost, inconsistently mapped, or require custom code in each service.
Current Problems and Anti-Patterns
Problem 1: Fragmented Header Mapping Solutions
Most services implement header mapping ad-hoc:
// Service A approach
func (s *ServiceA) CreateUser(ctx context.Context, req *pb.CreateUserRequest) (*pb.User, error) {
md, _ := metadata.FromIncomingContext(ctx)
authHeader := md.Get("authorization")
userID := md.Get("x-user-id")
// ... custom mapping logic
}
// Service B approach
func (s *ServiceB) GetOrder(ctx context.Context, req *pb.GetOrderRequest) (*pb.Order, error) {
// Different header names, different extraction logic
md, _ := metadata.FromIncomingContext(ctx)
auth := md.Get("auth") // Different from Service A!
requestID := md.Get("request_id") // Different format!
}
This leads to:
- Inconsistent header naming across services
- Duplicated mapping logic in every service
- Maintenance burden when headers change
- Testing complexity due to custom implementations
Problem 2: Context Abuse and Memory Issues
I have often observed misuse of Go’s context for storing large amounts of data that puts the service at risk of being killed due to OOM:
// ANTI-PATTERN: Storing large objects in context
type UserContext struct {
User *User // Large user object
Permissions []Permission // Array of permissions
Preferences *UserPrefs // User preferences
AuditLog []AuditEntry // Historical data
}
func StoreUserInContext(ctx context.Context, user *UserContext) context.Context {
return context.WithValue(ctx, "user", user) // BAD: Large object in context
}
Why This Causes Problems:
- Memory Leaks: Contexts are passed through the entire request chain and may not be garbage collected promptly
- Performance Degradation: Large context objects increase allocation pressure
- Goroutine Overhead: Each concurrent request carries this memory burden
- Service Instability: Under load, memory usage can spike and cause OOM kills
Proper Pattern:
// GOOD: Store only identifiers in context
func StoreUserIDInContext(ctx context.Context, userID string) context.Context {
return context.WithValue(ctx, "user_id", userID) // Small string only
}
// Fetch data when needed from database/cache
func GetUserFromContext(ctx context.Context) (*User, error) {
userID := ctx.Value("user_id").(string)
return userService.GetUser(userID) // Fetch from datastore
}
Problem 3: Inconsistent Response Header Handling
Setting response headers requires different approaches across the stack:
// gRPC: Set headers via metadata
grpc.SendHeader(ctx, metadata.New(map[string]string{
"x-server-version": "v1.2.0",
}))
// HTTP: Set headers on ResponseWriter
w.Header().Set("X-Server-Version", "v1.2.0")
// gRPC-Gateway: Headers must be set in specific metadata format
grpc.SetHeader(ctx, metadata.New(map[string]string{
"grpc-metadata-x-server-version": "v1.2.0", // Prefix required
}))
This complexity leads to missing response headers and inconsistent client experiences.
Solution: Standardized Header Mapping Middleware
The solution is a dedicated middleware that handles bidirectional header mapping declaratively, allowing services to focus on business logic while ensuring consistent header handling across the entire API surface.
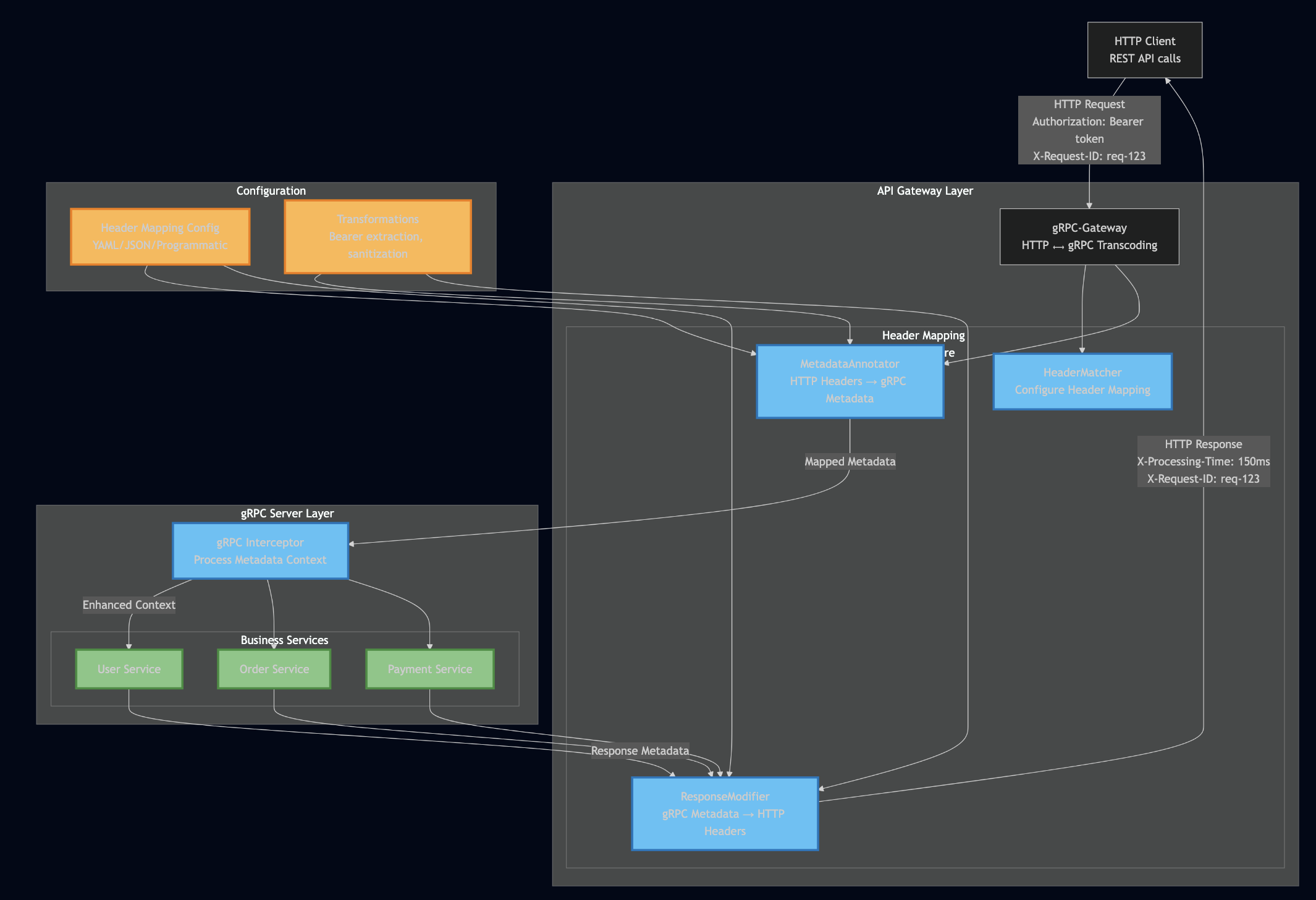
Core Architecture
HTTP Request ? Gateway Middleware ? gRPC Interceptor ? Service
? ? ? ?
HTTP Headers ? Metadata Annotation ? Context Metadata ? Business Logic
?
HTTP Response ? Response Modifier ? Header Metadata ? Service Response
The middleware operates at two key points:
- Gateway Level: Maps HTTP headers to gRPC metadata for incoming requests
- Interceptor Level: Processes metadata and manages response header mapping
Configuration-Driven Approach
Instead of custom code, header mapping is configured declaratively:
mapper := headermapper.NewBuilder().
// Authentication headers
AddIncomingMapping("Authorization", "authorization").WithRequired(true).
AddIncomingMapping("X-API-Key", "api-key").
// Request tracking (bidirectional)
AddBidirectionalMapping("X-Request-ID", "request-id").
AddBidirectionalMapping("X-Trace-ID", "trace-id").
// Response headers
AddOutgoingMapping("processing-time", "X-Processing-Time").
AddOutgoingMapping("server-version", "X-Server-Version").
// Transformations
AddIncomingMapping("Authorization", "auth-token").
WithTransform(headermapper.ChainTransforms(
headermapper.TrimSpace,
headermapper.RemovePrefix("Bearer "),
)).
Build()
This configuration drives all header mapping behavior without requiring service-specific code.
How The Middleware Works: Step-by-Step
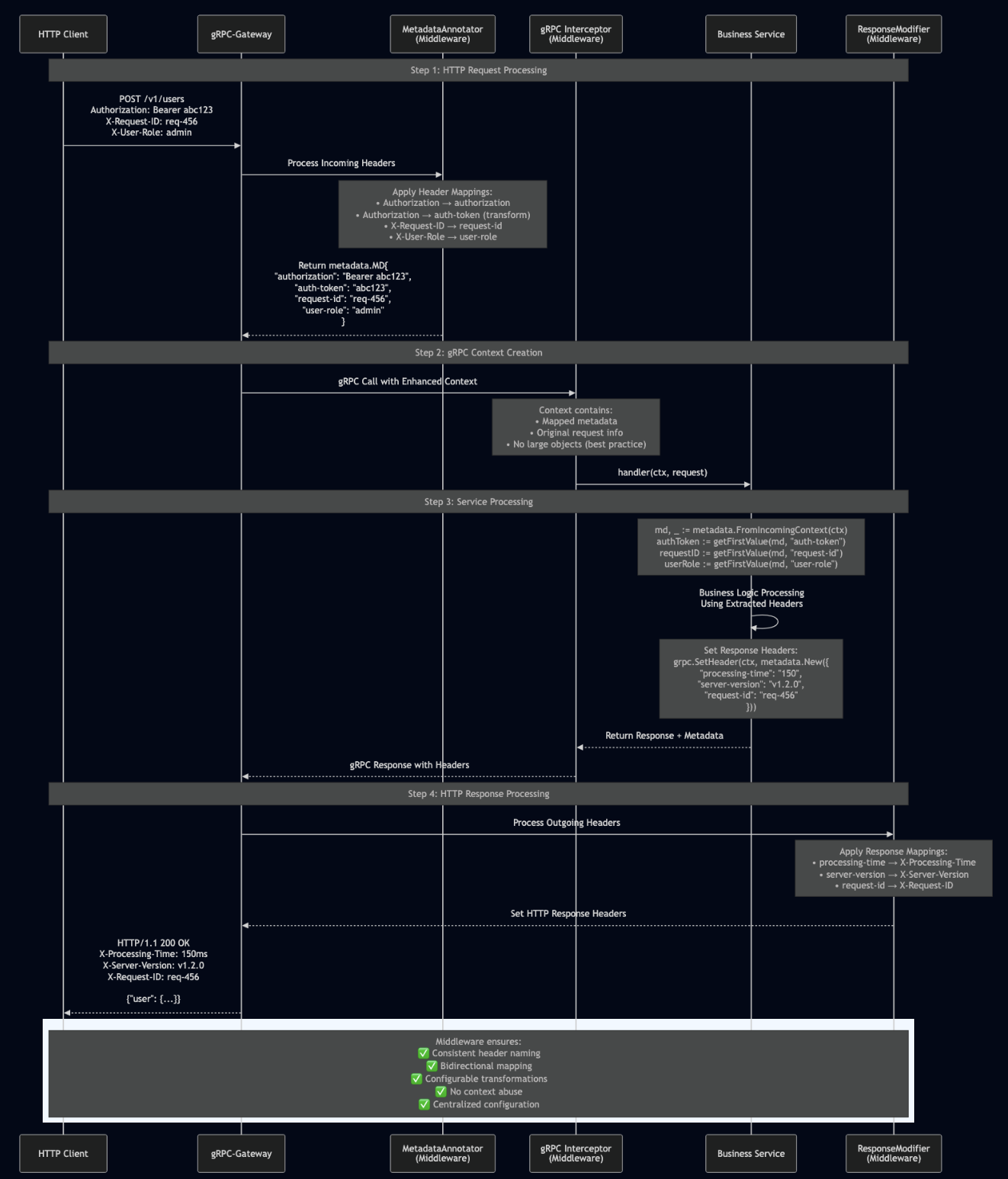
Step 1: HTTP Request Processing
When an HTTP request arrives at the gRPC-Gateway:
POST /v1/users HTTP/1.1 Authorization: Bearer abc123 X-Request-ID: req-456 X-User-Role: admin Content-Type: application/json
The MetadataAnnotator processes configured incoming mappings:
func (hm *HeaderMapper) MetadataAnnotator() func(context.Context, *http.Request) metadata.MD {
return func(ctx context.Context, req *http.Request) metadata.MD {
md := metadata.New(map[string]string{})
for _, mapping := range hm.config.Mappings {
if mapping.Direction == Outgoing {
continue // Skip outgoing-only mappings
}
headerValue := req.Header.Get(mapping.HTTPHeader)
if headerValue != "" {
// Apply transformations if configured
if mapping.Transform != nil {
headerValue = mapping.Transform(headerValue)
}
md.Set(mapping.GRPCMetadata, headerValue)
}
}
return md
}
}
Result: HTTP headers become gRPC metadata:
metadata.MD{
"authorization": []string{"Bearer abc123"},
"auth-token": []string{"abc123"}, // Transformed
"request-id": []string{"req-456"},
"user-role": []string{"admin"},
}
Step 2: gRPC Interceptor Processing
The gRPC unary interceptor receives the enhanced context:
func (hm *HeaderMapper) UnaryServerInterceptor() grpc.UnaryServerInterceptor {
return func(ctx context.Context, req interface{}, info *grpc.UnaryServerInfo, handler grpc.UnaryHandler) (interface{}, error) {
// Context already contains mapped metadata from Step 1
// Call the actual service method
resp, err := handler(ctx, req)
// Response headers are handled by ResponseModifier
return resp, err
}
}
Step 3: Service Implementation
The service method accesses headers through standard gRPC metadata APIs:
func (s *UserService) CreateUser(ctx context.Context, req *pb.CreateUserRequest) (*pb.User, error) {
md, _ := metadata.FromIncomingContext(ctx)
// Headers are consistently available
authToken := getFirstValue(md, "auth-token") // "abc123" (transformed)
requestID := getFirstValue(md, "request-id") // "req-456"
userRole := getFirstValue(md, "user-role") // "admin"
// Set response headers
grpc.SetHeader(ctx, metadata.New(map[string]string{
"processing-time": "150",
"server-version": "v1.2.0",
"request-id": requestID, // Echo back request ID
}))
return &pb.User{...}, nil
}
Step 4: Response Header Processing
The ResponseModifier maps gRPC metadata to HTTP response headers:
func (hm *HeaderMapper) ResponseModifier() func(context.Context, http.ResponseWriter, proto.Message) error {
return func(ctx context.Context, w http.ResponseWriter, msg proto.Message) error {
md, ok := runtime.ServerMetadataFromContext(ctx)
if !ok {
return nil
}
for _, mapping := range hm.config.Mappings {
if mapping.Direction == Incoming {
continue // Skip incoming-only mappings
}
values := md.HeaderMD.Get(mapping.GRPCMetadata)
if len(values) > 0 {
headerValue := values[0]
// Apply transformations
if mapping.Transform != nil {
headerValue = mapping.Transform(headerValue)
}
w.Header().Set(mapping.HTTPHeader, headerValue)
}
}
return nil
}
}
Final HTTP Response:
HTTP/1.1 200 OK
X-Request-ID: req-456
X-Processing-Time: 150ms
X-Server-Version: v1.2.0
Content-Type: application/json
{"user": {...}}
Advanced Features
Header Transformations
The middleware supports header value transformations:
// Extract JWT tokens
AddIncomingMapping("Authorization", "jwt-token").
WithTransform(headermapper.ChainTransforms(
headermapper.TrimSpace,
headermapper.RemovePrefix("Bearer "),
headermapper.Truncate(100), // Prevent large tokens
))
// Sanitize user agents
AddIncomingMapping("User-Agent", "client-info").
WithTransform(headermapper.RegexReplace(`\d+\.\d+(\.\d+)*`, "x.x.x"))
// Format timestamps
AddOutgoingMapping("response-time", "X-Response-Time").
WithTransform(headermapper.AddSuffix("ms"))
Configuration from Files
For complex deployments, configuration can be externalized:
# header-mapping.yaml
mappings:
- http_header: "Authorization"
grpc_metadata: "authorization"
direction: 0 # Incoming
required: true
- http_header: "X-Request-ID"
grpc_metadata: "request-id"
direction: 2 # Bidirectional
default_value: "auto-generated"
skip_paths:
- "/health"
- "/metrics"
debug: false
config, err := headermapper.LoadConfigFromFile("header-mapping.yaml")
if err != nil {
log.Fatal("Failed to load config:", err)
}
mapper := headermapper.NewHeaderMapper(config)
Path-Based Filtering
Skip header processing for specific endpoints:
mapper := headermapper.NewBuilder().
AddIncomingMapping("Authorization", "authorization").
SkipPaths("/health", "/metrics", "/debug"). // No auth required
Build()
Integration Guide
Basic Integration
package main
import (
"github.com/your-org/grpc-header-mapper/headermapper"
"github.com/grpc-ecosystem/grpc-gateway/v2/runtime"
)
func main() {
// Create header mapper
mapper := headermapper.NewBuilder().
AddIncomingMapping("Authorization", "authorization").
AddBidirectionalMapping("X-Request-ID", "request-id").
Build()
// Configure gRPC server
grpcServer := grpc.NewServer(
grpc.UnaryInterceptor(mapper.UnaryServerInterceptor()),
)
// Configure HTTP gateway
mux := headermapper.CreateGatewayMux(mapper)
// Register services...
}
Production Deployment
func createProductionMapper() *headermapper.HeaderMapper {
return headermapper.NewBuilder().
// Authentication
AddIncomingMapping("Authorization", "authorization").WithRequired(true).
AddIncomingMapping("X-API-Key", "api-key").
// Request correlation
AddBidirectionalMapping("X-Request-ID", "request-id").
AddBidirectionalMapping("X-Correlation-ID", "correlation-id").
AddBidirectionalMapping("X-Trace-ID", "trace-id").
// Client information
AddIncomingMapping("User-Agent", "user-agent").
AddIncomingMapping("X-Client-Version", "client-version").
// Response headers
AddOutgoingMapping("processing-time-ms", "X-Processing-Time").
AddOutgoingMapping("server-version", "X-Server-Version").
AddOutgoingMapping("rate-limit-remaining", "X-RateLimit-Remaining").
// Security headers
AddOutgoingMapping("content-security-policy", "Content-Security-Policy").
WithDefault("default-src 'self'").
// Skip system endpoints
SkipPaths("/health", "/metrics", "/debug", "/admin").
// Production settings
Debug(false).
OverwriteExisting(true).
Build()
}
Performance and Reliability Benefits
Consistent Memory Usage
By standardizing header extraction and avoiding context abuse, services maintain predictable memory profiles:
// Before: Inconsistent, potentially large context values
ctx = context.WithValue(ctx, "user", largeUserObject) // BAD
ctx = context.WithValue(ctx, "permissions", permissionList) // BAD
// After: Consistent, minimal context usage
// Headers extracted to standard metadata, large objects fetched on-demand
func GetUserFromContext(ctx context.Context) (*User, error) {
userID := getMetadata(ctx, "user-id")
return userCache.Get(userID) // Cached lookup
}
Reduced Code Duplication
Header mapping logic is centralized, eliminating per-service implementations:
Improved Observability
Consistent header handling enables better monitoring:
// All services automatically have request correlation
func (s *AnyService) AnyMethod(ctx context.Context, req *AnyRequest) (*AnyResponse, error) {
requestID := getMetadata(ctx, "request-id") // Always available
log.WithField("request_id", requestID).Info("Processing request")
// Business logic...
return response, nil
}
Testing Benefits
Standardized header mapping simplifies integration testing:
func TestServiceWithHeaders(t *testing.T) {
// Headers work consistently across all services
client := pb.NewUserServiceClient(conn)
ctx := metadata.NewOutgoingContext(context.Background(), metadata.New(map[string]string{
"authorization": "Bearer test-token",
"request-id": "test-req-123",
}))
resp, err := client.CreateUser(ctx, &pb.CreateUserRequest{...})
// Response headers are consistently available
md, _ := metadata.FromIncomingContext(ctx)
requestID := getMetadata(md, "request-id") // "test-req-123"
}
Security Considerations
Header Validation
The middleware supports header validation and sanitization:
mapper := headermapper.NewBuilder().
AddIncomingMapping("Authorization", "authorization").
WithTransform(headermapper.ChainTransforms(
headermapper.TrimSpace,
headermapper.Truncate(512), // Prevent oversized headers
validateJWTFormat, // Custom validation
)).
Build()
func validateJWTFormat(token string) string {
if !strings.HasPrefix(token, "Bearer ") {
return "invalid" // Reject malformed tokens
}
return token
}
Sensitive Data Handling
Headers containing sensitive data can be masked in logs:
AddIncomingMapping("Authorization", "authorization").
WithTransform(headermapper.MaskSensitive(4)). // Show first/last 4 chars
Rate Limiting Integration
Response headers can include rate limiting information:
AddOutgoingMapping("rate-limit-remaining", "X-RateLimit-Remaining").
AddOutgoingMapping("rate-limit-reset", "X-RateLimit-Reset").
Monitoring and Debugging
Debug Mode
Enable debug logging to verify header mapping:
mapper := headermapper.NewBuilder().
Debug(true). // Enable detailed logging
Build()
mapper.SetLogger(customLogger) // Use your logging framework
Debug Output:
[DEBUG] [HeaderMapper] Mapped incoming headers: map[authorization:[Bearer abc123] request-id:[req-456]] [DEBUG] [HeaderMapper] Mapped outgoing headers to response
Metrics Integration
The middleware can integrate with monitoring systems:
stats := mapper.GetStats() prometheus.IncomingHeadersMappedCounter.Add(stats.IncomingMappings) prometheus.OutgoingHeadersMappedCounter.Add(stats.OutgoingMappings) prometheus.MappingErrorsCounter.Add(stats.FailedMappings)
Why This Matters
Microservices Consistency
In large microservices architectures, inconsistent header handling creates operational overhead:
- Debugging becomes difficult when services use different header names
- Client libraries must handle different header formats per service
- Security policies cannot be uniformly enforced
- Observability suffers from inconsistent request correlation
Standardized header mapping addresses these issues by ensuring consistency across the entire service mesh.
Developer Productivity
Developers spend significant time on infrastructure concerns rather than business logic. This middleware eliminates:
- Boilerplate code for header extraction and response setting
- Testing complexity around header handling edge cases
- Documentation overhead for service-specific header requirements
- Bug investigation related to missing or malformed headers
Operational Excellence
Standard header mapping enables:
- Automated monitoring with consistent request correlation
- Security scanning with predictable header formats
- Performance analysis across service boundaries
- Compliance auditing with standardized access logging
Conclusion
HTTP and gRPC transcoding is a powerful pattern for modern APIs, but header mapping complexity has been a persistent challenge. The gRPC Header Mapper middleware presented in this article provides a solution that enables true bidirectional header mapping between HTTP and gRPC protocols.
By providing a standardized, configuration-driven middleware solution available at github.com/bhatti/grpc-header-mapper, teams can:
- Eliminate inconsistencies across services with bidirectional header mapping
- Reduce maintenance burden through centralized configuration
- Improve reliability by avoiding context misuse and memory leaks
- Enhance developer productivity by removing boilerplate code
- Support complex transformations with built-in and custom transformation functions
The middleware’s bidirectional mapping capability means that headers flow seamlessly in both directions – HTTP requests to gRPC metadata for service processing, and gRPC metadata back to HTTP response headers for client consumption. This eliminates the common problem where request headers are available to services but response headers are lost or inconsistently handled.
The complete implementation, examples, and documentation are available at github.com/bhatti/grpc-header-mapper.